As a web hosting company, many have expressed the opinion that Bluehost stinks:
- The Worst Web Host: Bluehost Sucks
- Why I will no longer use Bluehost as My WordPress Web Host
- Why Bloggers should Avoid Bluehost at All Costs
- Bluehost Sucks: Here’s How to Transfer Your Site to Siteground in Four Easy Steps
- Bluehost Sucks (not to be confused with …)
- Bluehost Sucks!!
- Sitelock Scam
I signed up for Bluehost 2½ years ago for a 3 year subscription at the rock bottom price of about $3.00 per month, paid in advance. I suspect they pack their servers with hundreds of websites and mine can really slow to a crawl. But, for someone who wants to learn about web development and has no plans to make money at it, the price cannot be beat.
I rarely need any support from Bluehost, but my site was recently hit by a malware attack. I now have something to say on the subject of: Does Bluehost suck?
The Malware Attack
The malware attack started on a Monday. Wordfence noticed that some files had changed, but Wordfence sends so many emails you can’t pay attention to them all and this one got by me until it was already too late.
On Tuesday morning, an email from SiteLock notified me that my site was infected. Bluehost uses SiteLock to scan it’s servers for problems. SiteLock will identify the problem, but if you need SiteLock to fix the problem, that costs extra.
On Tuesday afternoon, an email from Bluehost notified me that my site had been suspended because of the malware infestation. The email identified 8 infected files, directed me to clean the site before the suspension could be lifted, and cautioned that I might be asked to pack up and take my site elsewhere if it became necessary to deactivated my site 3 times within 60 days. They suggested I purchase a SiteLock subscriptions which would solve all of my problems.
That’s all pretty reasonable. Bluehost is cheap, cheap, cheap. I don’t expect them to clean my site if I get hacked. Moreover, my site sits on a shared server. They can’t take the chance that my infection will spread to other customers. My site is my responsibility. I get it.
I downloaded all of the files from the site so I could take a closer look from the safety of my laptop. I noticed a new file called malware.txt in the root directory. That file was VERY helpful. It was the full report generated by the SiteLock scan that first identified the problem. It identified 2600 infected files, not just the 8 listed by the Bluehost email. Egads. It’s a good thing I did not fix the 8 files and called it a job well done.
The day before the infection, I had downloaded all of the site files and data. That was very lucky. Restoring the clean files was easy. I had to hunt down some of the infected files myself, but that was not too hard.
I called Bluehost to let them know that the problem was solved and that the site should be reactivated. I was told that there would be another scan, and if it came back clean, the suspension would be lifted without delay.
Sadly, within a couple of hours, an email informed me that 2 infected files remained. Out of 2600 infected files, I missed only .00077%, not bad! It was easy to correct those last two files. Now, all I needed to do was let Bluehost know that the site was clean as a whistle and ready for reactivation.
And then I met Justin.
One Bad Apple Spoils the Bunch
I started a live chat with Justin at Bluehost tech support by trying to explain why I had missed the two files. It soon became clear that Justin had only one goal: to sell me expensive security services I did not want or need.
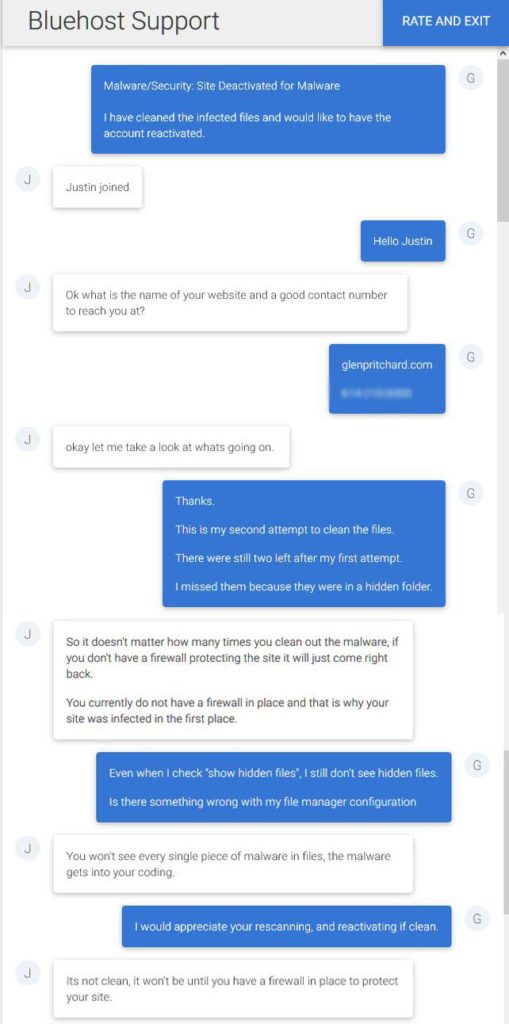
Hmm. I began to suspect that Justin had his own agenda. The trial lawyer in me kicked in: I needed to set the hook.
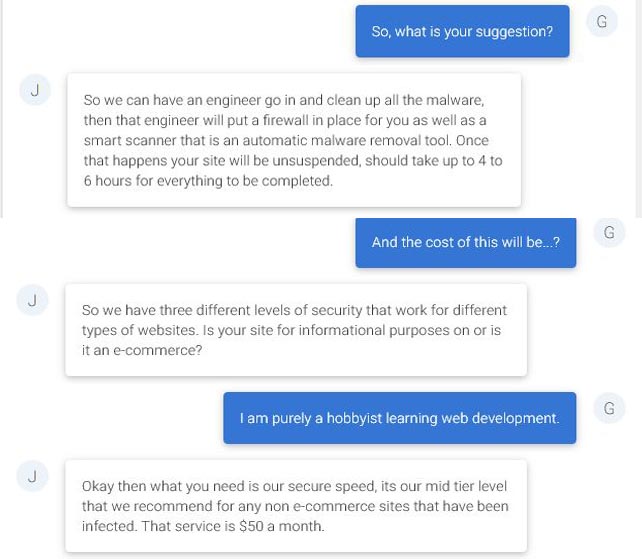
I laughed out loud. Fifty dollars a month would increase my cost by 1300%. Let’s see how far Justin is willing to go with this.
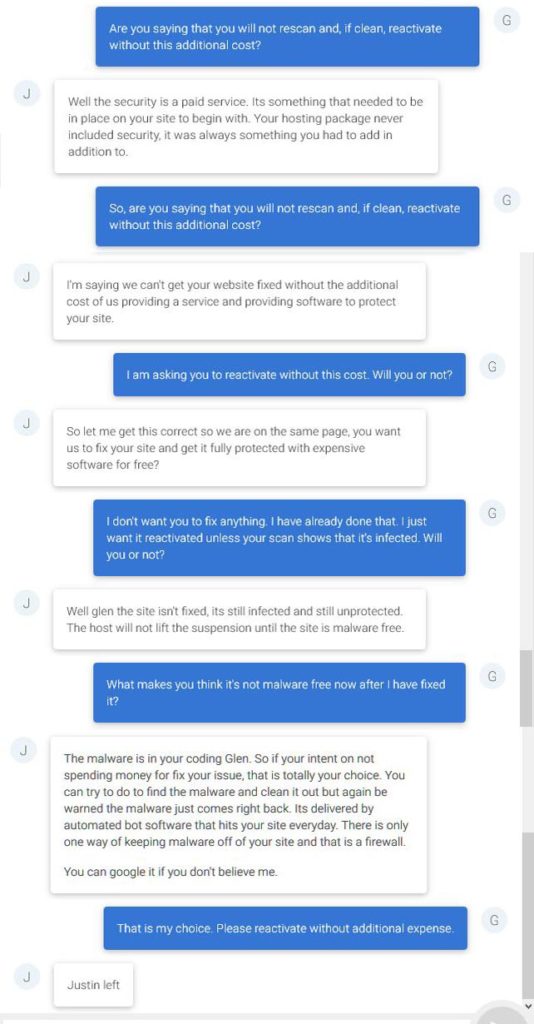
Wow. Justin hung up on me. He was not going to help unless he sold me that subscription.
I was livid. When you call Bluehost for support, you need to identify the reason for your call from a menu of options. There is no option to report tech support bullying. So, I used Bluehost’s Facebook page to send an instant message along with the screen shots of my encounter with Justin. To Bluehost’s credit, they got back to me right away. They confirmed that cleaning a malware infection is the customer’s responsibility, but buying a particular service is not required.
My Facebook contact assured me that my complaint about Justin would be “addressed to our leadership team for review and further action”. I have not heard anything about that. Justin may still be terrorizing other Bluehost customers. I wonder if they made him employee of the month.
A Happy Ending
After I ratted out Justin on Facebook, I called tech support about getting my account back online. He promptly scanned my site while I was on the line and confirmed that no further malware was detected. He said that my site would be restored within a few hours.
Twenty four hours later, the site was still inaccessible and it took another call to tech support to get it worked out. But, no big deal. These things happen.
So, Does Bluehost Suck?
Other than Justin, I interacted with 4 people at Bluehost tech support for help with the malware problem. They were all helpful, courteous and knowledgeable. Two of them suggested that SiteLock might be helpful, but neither pressured me after I rejected the idea.
This was a much better experience than 2 or 3 years ago when I last needed their help when a business website I manage became inaccessible. Bluehost had a glitch with the SSL certificate. I had to wait on hold for 20 to 40 minutes each time I wanted to followup with someone who had no idea what to do. After several days and countless hours with no resolution in sight, I gave up and moved the whole site to Siteground (where the service has been consistently excellent.)
Bluehost support has improved since then. I never had to wait to speak to someone, and they seemed to know exactly what to do and how to do it.
But it only takes one Justin to ruin a reputation.